An ongoing promotion dubbed Earth Bogle is leveraging political- themed hook to convey the NjRAT remote access troy to sufferers across the Middle East and North Africa.
"The threat actor uses public cloud storage services such as files[.] radio and failiem[.] lv to sponsor malware, while damaged web servers distribute NjRAT ", Trend Micro said in a paper published Wednesday.
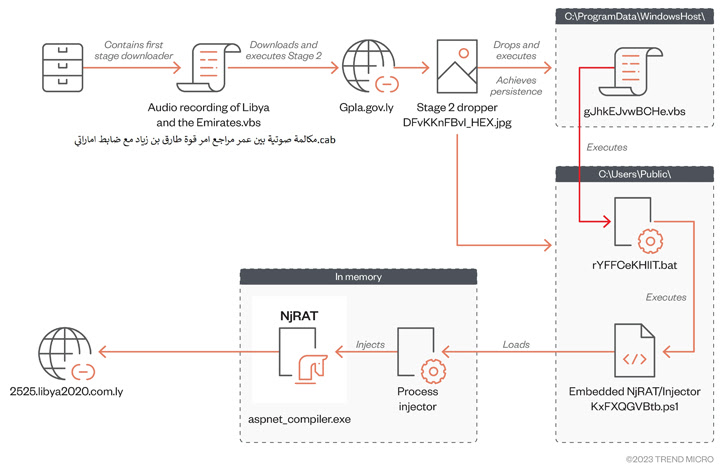
Phishing emails, usually tailored to the murderer's interests, are loaded with harmful attachments to unlock the infection routine. This takes the form of a Microsoft Cabinet( CAB) archive file containing a Visual Basic Script dropper to deploy the next- stage payload.
Nevertheless, it's suspected that the documents are distributed via social media platforms such as Facebook and Discord, in some cases just creating false accounts to provide ads on pages impersonating genuine information outlets.
The CAB files, hosted on cloud storage services, further masquerade as sympathetic voice calls to persuade the sufferer into opening the library, only for the VBScript to been executed, leading to the recovery of another VBScript document that masks itself as an image file.
In order to load and execute the RAT cargo, the second-stage VBScript retrieves a PowerShell script from an already compromised domain.
The danger professional can gather sensitive data and take control of compromised computers thanks to NjRAT( also known as Bladabindi), which was first identified in 2013.
The researchers came to the conclusion that "this case shows how threat actors will infect targeted populations by using public cloud storage as malware file servers and social engineering techniques that appeal to people's emotions like regional geopolitical themes as lures."
Follow Us on Telegram.

0 Comments